|
|
MSP10-512/256 Core 400G MACsec IP Core
|
|
|
General Description
Implementation of the new LAN security standard IEEE 802.1ae (MACsec) requires the NIST standard AES cipher in the GCM mode for encryption and message authentication, as well as header parsing and formatting operations on the transmitted and received packets. MACsec Security Processor (MSP) IP cores by IP Cores, Inc. are designed for high data rates and implement complete line-rate packet processing with no per-packet CPU intervention. The MSP10-512/256
cores are tuned up to 400 Gbps applications on modern FPGAs that require 256 bit AES keys.
The design is fully synchronous and available as RTL source code.
|
Key Features
- Small size combined with high performance:
- 100 Gbps performance at 315 MHz clock rate
- Self-contained
- Back-to-back packet processing
- 64 bytes shortest packet at full data rate
- Low fixed latency: 48 clocks input-to-output
- Two cores: MSP10-512E implements encryption for egress (Tx); MSP10-512E implements decryption for ingress (Rx).
-
Glueless or near-glueless interfaces to
MACs with 512 bits wide data buses.
- The MSP10-512E presents a sink interface to the system side, source interface for the MAC.
- MSP10-512D presents a sink to the MAC, source to the rest of the system.
-
Compatible with typical 100/400-Gbps Ethernet MACs
- MAC shall be configured to remove the preamble and FCS on Rx (default)
- Support for the 256 bit AES key per IEEE 802.1AEbn standard (128 bit version is also available)
- Simple microprocessor interface for control (address/data/write/read/read acknowledge). Adapters for popular microprocessor buses are available.
- Provides MACsec header parsing and modification:
- Insertion and removal of the SecTag including the packet number (PN) and an optional SCI
- RX packet validation
- Insertion, validation and removal of the ICV
- Replay protection based on the PN windowing
- Includes key storage, lookup, and expansion
- Configurable key lookup for Tx is based on MAC header (MAC addresses and VLAN)
- Key lookup for Rx is based either on MAC header or the SCI
- Support for Galois Counter Mode Encryption and authentication (GCM), Galois Message Authentication (GMAC)
- Support for Extended Packet Numbering per IEEE 802.1AEbw (GCM-AES-XPN-256)
- Flow-through design
- Test bench provided
- Sample software for 802.1X-2010 (a.k.a. 802.1af, KEYsec, 802.1x-REV) key agreement (MKA) is provided
- Deliverables include test benches and optional NIST algorithm validation
|
Applications
|
|
Symbols
 |
|
|
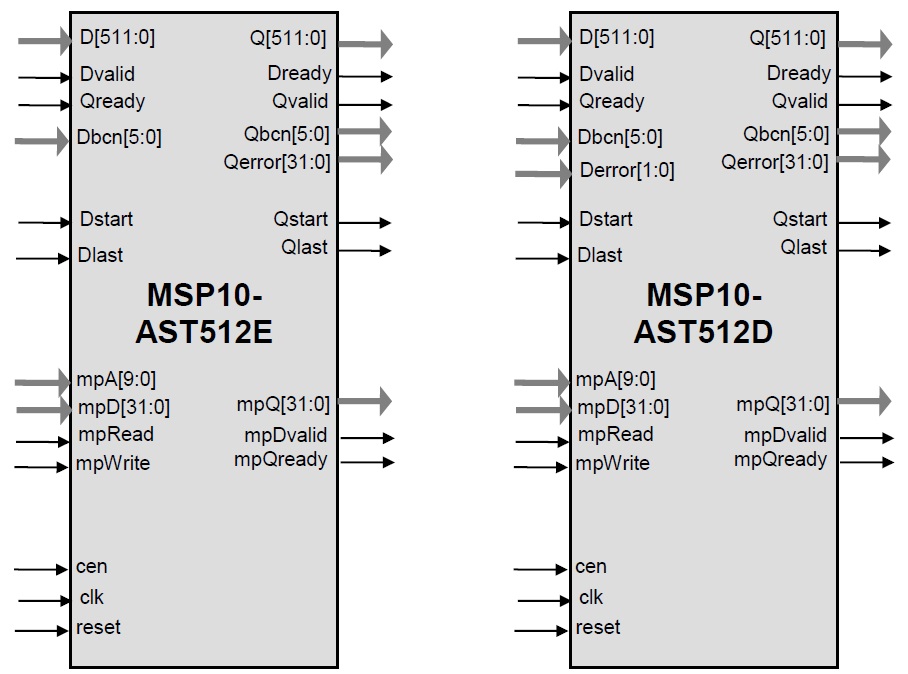
Pin Description
| Name |
Type |
Description |
Generic |
| Clk |
Input |
Core clock signal |
| reset |
Input |
Core reset signal |
| cen |
Input |
Synchronous enable signal. When LOW the core ignores all its inputs and all its outputs must be ignored. |
Sink Interface |
| D[511:0] |
Input |
Databus data signal |
| Dready |
Output |
Databus ready signal |
| Dvalid |
Input |
Databus valid signal |
| Dstart |
Input |
Databus startofpacket signal. Indicates that the first word of the input packet is driven into the core on the D bus. |
| Dlast |
Input |
Databus endofpacket signal |
| Dbcn[5:0] |
Input |
Databus empty signal. Asserted together with last, indicates the number of unused bytes in the LSB of the D bus. |
| Derror[1:0] |
Input |
Databus error signal. MSP10-512D only. Allows the core to receive the Rx error indicators (typically fcs_error and rx_error) from the MAC. The core does not interpret these and simply passes them through to the source interface alongside with its own errors. |
Source Interface |
| Q[511:0] |
Output |
Databus data signal |
| Qready |
Input |
Databus ready signal |
| Qvalid |
Output |
Databus valid signal |
| Qstart |
Output |
Databus startofpacket signal. Indicates that the first word of the input packet is driven by the core onto the Q bus. |
| Qlast |
Output |
Databus endofpacket signal |
| Qbcn[5:0] |
Output |
Databus empty signal. Asserted together with last, indicates the number of unused bytes in the LSB of the D bus. |
| Qerror[31:0] |
Output |
Databus error signal. Can be asserted at different times and usually indicates the need for the external circuitry to take specific action (see the details below). |
Configuration. The signals in this group typically have constant values during the core operation |
| encrypt |
Input |
When HIGH, core is encrypting, when LOW core is decrypting |
CPU interface |
| mpA[9:0] |
Input |
Address |
| mpD[31:0] |
Input |
Write data |
| mpQ[31:0] |
Output |
Read data |
| mpRead |
Input |
When HIGH, read operation |
| mpWrite |
Input |
When HIGH, write operation |
| mpDvalid |
Output |
When HIGH, valid data are available on the mpQ bus |
| mpQready |
Output |
When HIGH, CPU can write to the mpD bus |
|
|
| |
|
| |
Tx Processing (MSP10-512E)
On encryption, for each frame the core:
- Obtains the SC index based on the MAC header and VLAN information and looks up the current SA key
- Inserts the SecTag, including the PN and an optional SCI
- Encrypts and authenticates the frame, based on the values on the E and C inputs
- Appends the ICV tag to the packets
- Updates the PN
- Updates the statistics counters
|
|
| |
Rx Processing
On decryption, for each frame the core:
- Obtains the SC index from the SCI (or fixed if SCI is not present) and looks up the current SA key
- Validates the SecTag and SCI, if present
- Checks that the packet number PN is within the PN window
- Decrypts the frame, if encrypted
- Calculates the ICV tag, if the frame is authenticated, and compares to the one in the frame
- Removes the ICV tag, appended to the frame
- Updates the PN window
- Updates the statistics counters
|
|
| |
|